CIA Agents in East Germany; Documents of the Secret Writing Method and Decipher Materials of the Stasi Records Agency
This is an excerpt of a German language document publicly available in the site containing STASI decipher service documents. The material contains information obtained by counter-intelligence of the Democratic Republic of Germany about CIA numbers stations. The report describes the use of cipher message, and its transmission through radio waves and receiving it. Furthermore, the text shows example of deciphering the numbers station message. The context of the document shows that STASI had decoded real CIA messages however, they are not available in public. This document is concrete example that numbers stations are used by intelligence agencies and shows its usage in depth.
District administrative Frankfurt (O) 06 08 81
State Security Tel. 2236/2524/81
Division II
IMB “Wave”
Please find find 80 photocopies within enclosed package of decipher tables for decryption.
Radio messages and the opening report
For OV “Hans”

Below is a description of the archive package and its contents.
Content: – 1 000 DDR Marks
– Instruction receiving and decrypting radio broadcasts
– Plastic card for substitution numbers – letters
– Decipher table 33/0254
– Instructions of the cryptography method (copying method)
– List the contents of the package and work instructions
Here is a guide for using the cipher method. There is a copying method, equal to the copy paper and perforating paper process, we only applied the chemical substances on the paper outbox. It is transmitted in plain text. But that’s not the subject of these pages.
INSTRUCTIONS for receiving and DECODING RADIO MESSAGE:
1. INTRODUCTION:
The purpose of this briefing is to explain a radio system that works quickly and reliable on a shortwave broadcast at predetermined times and frequencies.
2. TIMETABLE:
There are at _______________; ______________ and ______________ to ________ and _______transmit. You have the following frequencies allocated ____________, ________ _______ And. If the selected frequency on the first received signal is unclear, try one of the other specified frequencies. It is not necessary to receive all scheduled transmissions. Follow exact details.
3. RADIO:
A good receiver with a shortwave reception from 3.0 to 18 MHz (100 to 16 meters) is needed for the reception of the broadcasts. For reasons of personal safety, it is recommended to use a headset.
4. RECEPTION OF THE RADIO MESSAGE:
a. Shortly before the scheduled reception time, set the radio at on the predetermined frequency. Sometimes it can be difficult to hear the message because of noise or another frequency for your frequency is occupied by other stations. However, accurate and constant handling of the radio enables reception despite the maximum disturbance. Radio scales are not always accurate – that’s why it is sometimes necessary for the dial button to be carefully turned to the left or right so the message can be readily received. Sometimes not all clocks are accurate, so you dont not need to worry if the consignment is not on even radioed time.
b. Listen to the radio for long until you find a three-digit number
(Notification mark), is sent three times, a five-digit number
(Line number); and finally, a two or three-digit number
(Group number) have received such. B .: 124 124 124 36158 13. Write the numbers at once. These nine or ten digits are called message headers.
The message header is transmitted for five minutes. Then, you hear five one second tone (message alert tones); immediately followed by the message
(Each number group is sent only once); then repeat the word, and the repetition of the message; at the end of the word.
c. The following encrypted message can exercise through the matrix decipher table.
(Usually a part of the Decipher blocks) and through the Matrix to be decrypted (See § 5 c)
07070 25659 66445 34930 79507 82080 27771 19786 15656 09584 29381 47091
69072 END.
Remember that each group number (five-digit number) is spoken only once, but that the entire message in each transmission is repeated once.
d. The first three-digit number in the message header is the message indicator (Here 124) indicates whether the message is new or just a repetition, and whether the message is indicated for you. When a few days later the same thing – message indicator is again transmitted it simply means that its a repetition of the old message. New messages are always have a new characteristics.
e. The five-digit number group in the notification header (here 36158) shares the exact line of decipher blocks with where the decryption process begins. That is why it is called line label. She is always in the to be found in the left-hand column of the current affected side. In this example, 36158 applies as the first group of numbers (in the left column Table in § 5 c,of these allusions).
f. The last two or three-digit numbers (here 13), in the group number, shows you how many number groups are included in the message.
g. When you hear the five one-second tones, you should be prepared to write down that message. Write the message so that between the lines you have enough space, unhindered for deciphering.
EXAMPLE:
MESSAGE: 07070 25659 66445 34930 79507 82080 27771 19786 15656 etc
TABLE: _____ _____ _____ _____ _____ _____ _____ _____ _____
TOTAL: _____ _____ _____ _____ _____ _____ _____ _____ _____
5. decipher:
a. After you have written down the message, you will find the line label in the left column of decipher blocks, the line label is always the first group of numbers in the left column of the first line after the last completely or partly used line. In our example, 62530 (line 2 of Table) the last number used group of decipher blocks; so should 66253 (row 3 of the table), be the line number for the next radio message. The first group of numbers of line number is the group where the decipher process begins. The group number is 13. So for the exercise message we need 13 groups of numbers to decipher the exercise message. The first thirteen sets of numbers is the number group of line number. The line label itself is never used when deciphering.
EXAMPLE
MESSAGE: 07070 25659 66445 34930 79507 82080 27771 19786 15656 etc
BLOCK: 39920 84927 75423 43123 65448 95367 47077 68398 62530 etc
TOTAL: _____ _____ _____ _____ _____ _____ _____ _____ _____
b. Here is an example of decipher process for exercise in message
Paragraph 4, where the number of groups and the message of decipher blocks are added together by a peculiar counting method.
The result is a new point groups, five-digit numbers. If the sum of two digits (10 or higher than 10) is the one dropped, e.g. the first group of the message and the block is 36990th If you 7 and 9 counts up, they receive 6 instead of 16th
MESSAGE: 07070 25659 66445 34930 79507 82080 27771 19786 15656 etc
BLOCK: 39920 84927 75423 43123 65448 95367 47077 68398 62530 etc
Total: 36990 09576 31868 77054 34945 77347 64748 77074 77186
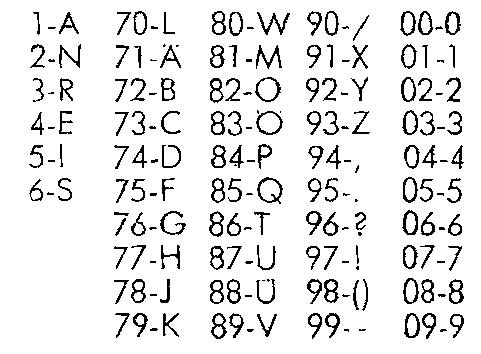
c. Then, convert the numbers into letters to the obtain the actual message. To do this, use the number-letter card (Matrix) on this page. The sums are decoded from left to right. There it should be ensured that some, often occurring characters with single-digit numbers match, while all other letters double-digit numbers have combinations. Figures represent two-digit numbers with the a 0 start. e.g. 84 results P. 6 gives S and 09 gives the number. 9 Please decrypt the other sets of numbers, accordingly.
EXAMPLE:
Total: 36990 09576 31868 77054 34945 77347 64748 77074 77186
TEXT: RM-0 ___
………………………………………….. ……………………
Matrix Decipher table
1-A 70-L 80-N 90- / 00-0 36158 39920 84927 75423 43124
2-N-71 Ä 81-M 91-X 01-1 65448 95367 47077 68398 62530
3-R 72-B-82 92 O-Y 02-2 66253 58366 61286 69623 89479
4-E 73-C 83-E 93-Z 03-3 22781 35802 26913 52697 54330
5-I-74-D 84 P 94-, 04-4 44896 80954 53014 46519 18061
6-S 75-F 85-Q 95. 05-5 33050 53202 88903 09695 44661
76-G 86 T 96-? 06-6 35924 68811 41070 14781 12935
77-H-87 U 97! 07-7 74853 17191 39250 99372 13425
78-J-88 Ü 98- () 08-8 63338 80660 61262 02957 30867
79-K 89-V 99– 09-9 21344 86559 84002 00850 49681
18677 90931 40678 53304 079
38391 63768 36076 73238 32353
Note: In the original document the manual 80-N is entered.
It is not the right Matrix!
6. CHECKLIST:
a. pre-encrypted message to listen carefully and write down.
b. Find line label on the decipher block.
c. The number groups are required to be written down in blocks. Do not forget that the line label itself is not one of those number groups.
d. The groups the message with the retrieved groups out of decipher tables are totaling (due to incorrect addition).
e. Covert sums of false addition in letters (using of template)
f. Burn all written down decipher materials and hide them.
g. PROCEDURE: To change the frequency and broadcasting time. Every now and then it may be necessary, the frequencies and or times of the schedule can change. In this case, you will have the details within the transmitted message.
h. Safety:. Each received message will have a message sequence number. Through secret writing connection, the number is known from the last recorded message and the quality of reception With this information we can create a preserve intact system. After one side of the comparison decipher blocks it’s necessary to, tear off the page and burn it. Whenever as possible you have to burn all papers, during the decryption process. Keep the decipher block, figures and letters and One time pad and this instruction in a safe hiding place.
Programming schedule:
during the summer months:
Wednesday – 1800 GMT (2000 local time)
Saturday – 1800 GMT (2000 local time)
Sunday – 0500 GMT (0700 local time)
during the winter months:
Wednesday – 1800 GMT (1900 local time)
Saturday – 1800 GMT (1900 local time)
Sunday – 0500 GMT (0600 local time)
Matrix plastic card:
Author’s note:
It’s not in particularly trustful form to issue information about a secret writing method without encryption! I find it extremely insecure that the decipher table must be destroyed only after completing consumption! Continuous destruction protects already received information and completed orders!
Analysis of the OTP from the process
These documents currently have no cryptologic analysis.
Therefore assign, security.
My analysis shows:
– The OTP consists of 80 sheets, each with 25 rows and 5 columns filled with five groups. Accordingly 10,000 five groups.
– Consideration is only 1% of the five groups twice to four times!
921 double-, 18 triple and 1 fourfold group of five.
Here is an instruction for creating CIA OTP Keys.
Here is a complete set of the 80 OTP.
Formation of call signs, in CIA secret broadcast is described in the GDR book “Caught in the Middle”
In the book “Caught in the Middle” by Heinz Günther, page 67 contains concrete example of a CIA secret broadcast described as the radio operator makes his call sign table.
Quote:
In this case a phrase is used from the novel:
by Theodor Fontane, “The Stechlin”, old Dubslav says:
“There is a lady and a woman in the room at the same time” (“DAS IST EINE DAME UND EIN FRAUENZIMMER ZUGLEICH)
Here we wrote a table in the header are the days of the month starting with the first and ending with the thirty-first.
Sources:
1) Der Der SAS- und Chiffrierdienst (SCD).ZCO und das ZfCh http://scz.bplaced.net/mfs_zco.html#matrix




